 |
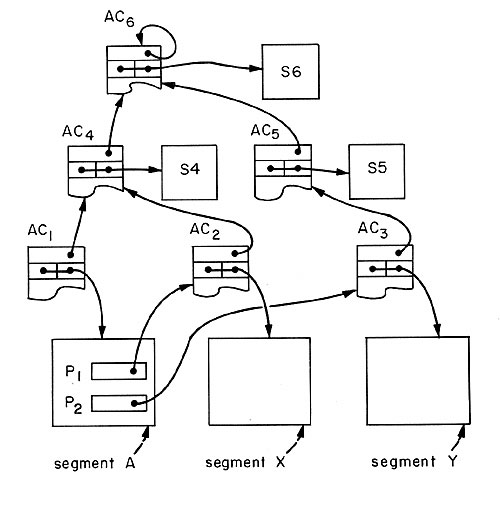
| Fig. 13. Hierarchical control of authority to modify access control lists. Each access controller has an extra field in addition to those of Fig. 12; the extra field contains the unique identifier of some higher level access controller. Authority to access segments A, X, and Y is controlled by access controllers AC1, AC2, and AC3, respectively. Authority to modify AC1 and AC2: is in turn controlled by AC4, while authority to modify AC3 is controlled by AC5. Authority to modify AC4 and AC5, is controlled by AC6, which is the first access controller in the system. In this example, the authority to modify AC6 is similar to the self-control scheme. Note that segments S4, S5, and S6 may be degenerate; AC4, AC5, and AC6 may exist solely to control the authority to modify other access controllers. The meaning of the backpointer, say, from AC1 to AC1, is that if a user attempts to modify the access control list of AC1, the backpointer is foUowed, leading to AC1. Only if the user's principal identifier h found in AC4 (with appropriate permission) is the modification to AC1 permitted. Segments A, X, and Y are arranged in an independent hierarchy of their own, with A superior to X and Y, by virtue of the pointer values P1 and P2 found in segment A. |